The Password Revolution - From Complex Confusion to Passphrase Power
In 2011, a simple six-panel comic changed the cybersecurity world forever. XKCD 936 by Randall Munroe demonstrated with elegant simplicity that everything we thought we knew about password security was backwards.
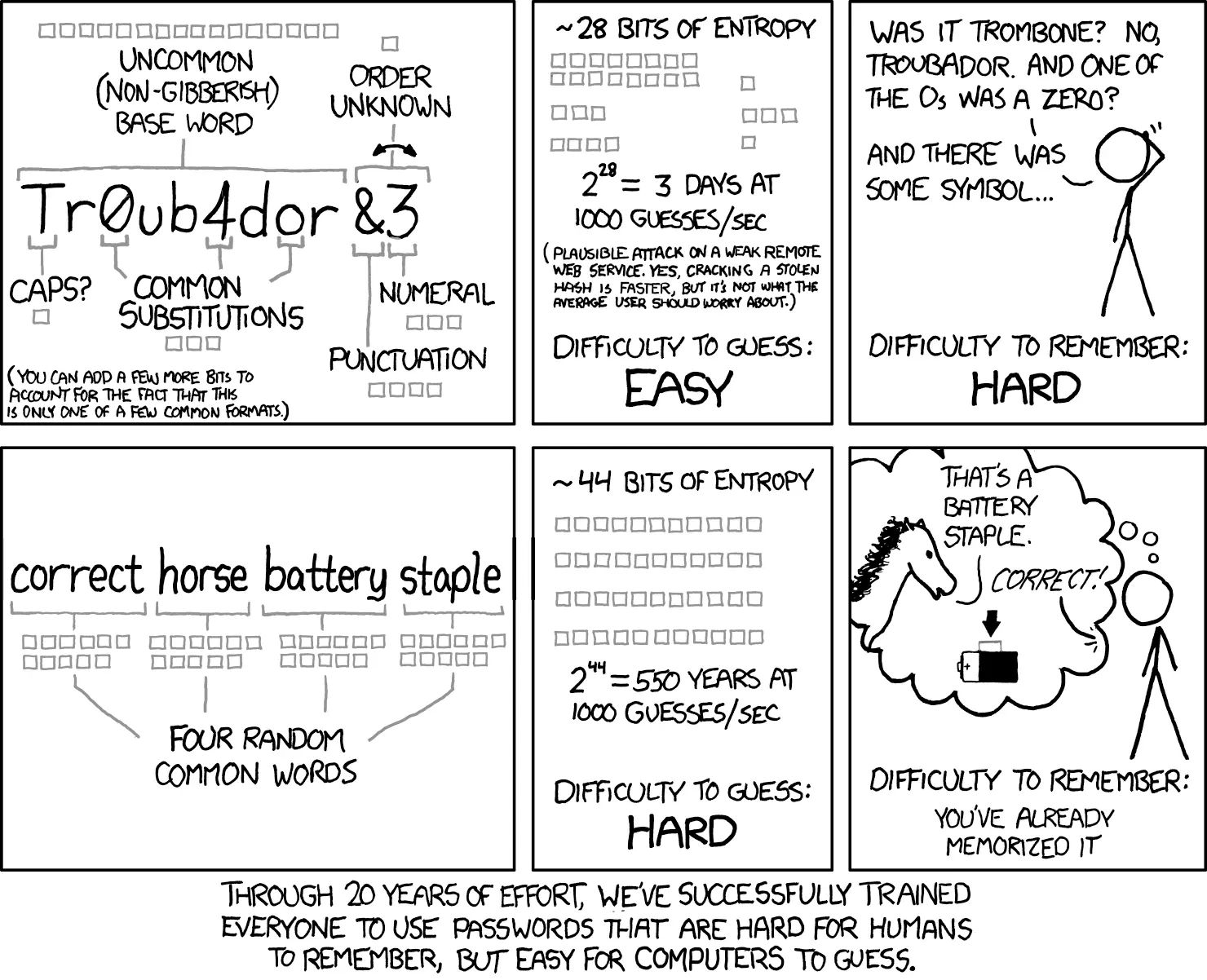
Randall Munrow comic
Today, in 2025, government agencies and cybersecurity experts have finally caught up to what that comic taught us over a decade ago.
The comic’s message was revolutionary: “Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
The Old Way: Making Humans Suffer for No Security Gain
For decades, IT departments tortured users with password requirements that seemed designed by sadists:
- Must contain uppercase and lowercase letters
- Must include numbers and special characters
- Must be changed every 90 days
- Cannot reuse the last 12 passwords
- Cannot contain dictionary words
This resulted in the predictable pattern: Password123! → Password124! →
Password125!
The problem? These “complex” passwords are actually weak. Modern
password-cracking tools easily handle substitutions like @ for a or 3 for
e. Meanwhile, users, unable to remember these cryptic combinations, wrote them
on sticky notes or stored them in browser auto-complete.
The Science: Why Length Beats Complexity
Password strength is measured in “bits of entropy” - essentially how many guesses an attacker would need to crack your password. The formula is surprisingly simple:
Entropy = Password Length × log₂(Character Set Size)
Let’s compare the comic’s famous examples:
Traditional “Complex” Password: Tr0ub4dor&3
- Length: 11 characters
- Character set: ~94 (upper, lower, numbers, symbols)
- Entropy: ~72 bits
- Human experience: Impossible to remember, written on sticky note
Modern Passphrase: correct horse battery staple
- Length: 25 characters
- Character set: ~27 (lowercase + space)
- Entropy: ~118 bits
- Human experience: Easy to remember, never written down
The winner? The passphrase is dramatically more secure (118 vs 72 bits) while being infinitely easier for humans to use.
Government Guidelines Have Caught Up
The National Institute of Standards and Technology (NIST) has completely reversed course. Their 2025 guidelines now recommend:
What’s IN:
- Minimum 15 characters (NIST standard - insufficient for passphrases without entropy testing)
- Support all characters including spaces and Unicode
- Allow copy-paste to enable password managers
- Screen against breached passwords using databases like HaveIBeenPwned
- Use password managers (explicitly recommended)
Rhodium Systems Recommendation: While NIST specifies 15 characters minimum, this is insufficient for simple passphrases. Without entropy testing, require 24+ characters to ensure adequate security with typical word-based passwords.
What’s OUT:
- ❌ Complexity requirements (no more mandatory special characters)
- ❌ Regular password changes (change only when compromised)
- ❌ Dictionary word prohibitions (passphrases are encouraged)
- ❌ Security questions (often weaker than passwords themselves)
The Cybersecurity & Infrastructure Security Agency (CISA) goes even further, recommending 16+ character passwords and strongly encouraging password manager adoption across all organizations.
The Rhodium Systems Approach: Entropy-Based Validation
At Rhodium Systems, we’ve implemented these modern principles in our ResorsIT authentication systems. Instead of arbitrary complexity rules, we use mathematical entropy calculation:
function calculatePasswordEntropy(password) {
let charSetSize = 0;
if (/[a-z]/.test(password)) charSetSize += 26;
if (/[A-Z]/.test(password)) charSetSize += 26;
if (/[0-9]/.test(password)) charSetSize += 10;
if (/[^a-zA-Z0-9]/.test(password)) charSetSize += 32;
return password.length * Math.log2(charSetSize || 1);
}
Our system provides real-time feedback showing users exactly how secure their password is, encouraging longer passphrases while allowing total flexibility in character choice.
Regular users need: 50+ bits of entropy (typically 24+ characters for passphrases) Admin users need: 70+ bits of entropy (typically 30+ characters for passphrases)
Creating Secure Passwords: Different Types for Different Needs
The key to good password security is matching the approach to the authentication type. Modern systems require four distinct password strategies:
For Regular User Accounts (24+ characters)
Person-to-computer authentication where you need to remember the password. Given that English words average 5 characters plus spaces, you need at least 4 words to reach the 24-character minimum. Here are proven methods for human-memorable passwords:
Method 1: Random Words Use 4-6 random common words:
ocean purple telescope sandwichmountain coffee digital butterfly- Tools like Diceware or correcthorsebatterystaple.net can generate these
Method 2: Modified Phrases Take a known phrase and alter it:
- “Lucy in the sky with Diamonds” →
Lucy in the sky with Rubies - “Ask not for whom the bell tolls it tolls for thee” →
Ask not for whom the bell tolls it tolls for Some Dude
Critical note: Don’t use these exact examples! They’re now famous and will appear in password dictionaries.
Method 3: Personal but Obscure Create phrases meaningful to you but impossible for others to guess:
Purple Rain Dances Across Midnight BridgesCoffee Shops Never Close During Finals Week
Important Warning: Don’t use phrases that people regularly hear you say. For example, if you’re known for saying “Onward Forward or Some Direction” in meetings or conversations, this becomes guessable through social engineering. Choose phrases that are personally meaningful but not part of your verbal habits or public persona.
For Password Manager Master Keys (36+ characters)
Master keys (note: “master” refers to a master key, not master/slave terminology - this term has been used in cryptography for decades) require special consideration since they protect all your other passwords:
Extra Length Required: Master keys should be at least 6 words (36+ characters minimum) for maximum security, since they protect all your other passwords.
Maximum Entropy: Use the full range of characters - uppercase, lowercase, numbers, and symbols when possible.
Memorable but Unique: You can’t store this password anywhere else, so it must be memorizable yet completely unique.
Examples (don’t use these - create your own):
The Quick Brown Fox Jumps Over Thirteen Lazy Dogs Today!Coffee Plus Moonlight Equals Perfect Coding Sessions Every Night at 3AMMy Favorite Mystery Book Always Has Exactly 47 Chapters & 1,247 Pages
For Computer-to-Computer Authentication (32+ characters)
Systems authenticating to other systems should use randomly generated passwords that humans never need to remember:
Full Random Generation: Use cryptographically secure random generators to create completely random passwords.
Maximum Length: Use the longest passwords the system supports - typically 32, 64, or even 128 characters.
Automatic Rotation: These passwords should rotate frequently (weekly or monthly) using automated secret management systems.
Examples (generated randomly):
K7$mP9#vL2&nQ5*wR8@xT1^yU4%zE6!aS3(dF0)gHX9k$L2m@N5p#Q8r&T1v^Y4w*Z7x!A0b(C3e)F6h+J9k
Secret Management Tools: Use systems like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault for automatic generation and rotation.
For Most Other Accounts: Use Password Managers
For the majority of your accounts, don’t create passwords manually at all.
The Password Manager Solution
While creating memorable passphrases works for primary accounts, the reality is that we all have dozens of accounts, and some of us have hundreds. The solution? Password managers.
Both NIST and CISA explicitly recommend password managers because they:
- Generate cryptographically random passwords
- Store them with military-grade encryption
- Autofill to prevent keylogger attacks
- Audit existing passwords for weakness
- Alert about breached accounts
Recommended enterprise options include:
- 1Password - Strong security track record with no major data breaches
- Bitwarden - Open-source with no major breaches, though some minor vulnerabilities addressed
- Keeper - No data breaches, though had some browser plugin vulnerabilities
Note: We do not currently recommend LastPass due to serious security breaches in 2022 that compromised customer vault data and continue to result in cryptocurrency thefts through 2025.
The key is choosing a reputable password manager and using it consistently.
What You Should Never Do
Despite the new guidance, these practices remain dangerous:
- ❌ Using the same password in more than one place - The #1 cause of account compromise
- ❌ Writing passwords on sticky notes - Physical security matters too
- ❌ Sharing passwords with colleagues - Each person needs unique access
- ❌ Using personal information - Names, birthdays, addresses are easily guessed
- ❌ Ignoring breach notifications - Change passwords immediately when services are compromised
The Security Question Problem
While modern systems are moving away from security questions (NIST now recommends against them), many legacy systems still use them. If you encounter security questions, never give the correct answer.
Security questions are fundamentally flawed because:
- The answers are often publicly discoverable through social media
- Attackers can use social engineering to gather the information
- Family and friends know many of the answers
- The answers never change, creating permanent vulnerabilities
The Solution: Treat Security Questions Like Passwords
Instead of answering “What was your first car?” with “Dodge Dart”, use a random, unguessable response like “a small furry wombat” or “purple elephant tornado”.
Examples of Better Security Question Answers:
- Question: “What was your first pet’s name?” → Answer: “quantum mechanical banana”
- Question: “What street did you grow up on?” → Answer: “rainbow bridge avenue”
- Question: “What was your mother’s maiden name?” → Answer: “cybernetic butterfly”
Store these fake answers in your password manager just like any other password. This approach eliminates the social engineering vulnerability while maintaining the recovery functionality.
Implementation for Organizations
If you’re responsible for organizational password policy, here’s a modern approach:
Updated Policy Template:
PASSWORD REQUIREMENTS:
- Minimum 24 characters (30+ for administrative accounts)
- Exception: Systems with entropy testing may accept 15+ characters
- All printable characters allowed including spaces
- Must be unique across all systems
- Change only when compromised or suspected compromise
TOOLS PROVIDED:
- Company-licensed password manager
- Multi-factor authentication on all accounts
- Breach monitoring service
PROHIBITED:
- Password reuse across systems
- Sharing passwords with others
- Storing passwords in unsecured locations
Technical Implementation:
- Replace complexity checks with entropy calculation
- Integrate with breach databases (HaveIBeenPwned API)
- Support copy-paste functionality
- Allow Unicode characters and spaces
- Set reasonable maximum length (64+ characters)
The Future: Beyond Passwords
While we’re making passwords more human-friendly, the industry is simultaneously moving toward passwordless authentication:
- Passkeys using FIDO2/WebAuthn standards
- Hardware tokens like YubiKeys
- Biometric authentication with proper privacy protection
- Magic links for low-security applications
Important caveat: None of these passwordless technologies have been tested by time. It took decades to discover the real-world issues with traditional passwords - these new systems may have problems that haven’t been found yet because they’re not in heavy use. Adding passwordless methods to complement passwords can’t make security worse than passwords alone, but relying on them exclusively means going out on the cutting edge.
These technologies promise to eliminate password-related breaches entirely, but we’re still years away from universal adoption and proven long-term security.
Real-World Impact
Organizations implementing modern password practices report:
- 75% reduction in password-related helpdesk tickets
- 90% improvement in password uniqueness compliance
- 60% reduction in successful phishing attacks
- Significant improvement in user satisfaction with security systems
The key insight: Security and usability don’t have to be opposites. When we align security requirements with human psychology, we get better outcomes for everyone.
Conclusion: The XKCD Legacy
Fourteen years after that famous comic, we’re finally implementing its wisdom at scale. The password revolution isn’t just about better entropy calculations or government guidelines - it’s about recognizing that humans are part of the security system, not obstacles to overcome.
The old way: Complex rules that created weak, unusable passwords The new way: Simple principle that creates strong, memorable passwords
Remember: Lucy in the sky with Rubies really is more secure than Tr0ub4dor&3,
and now the math, the government, and the user experience all agree.
As Randall Munroe demonstrated in six simple panels, sometimes the most profound insights are also the most obvious - we just needed to stop making passwords hard for humans and easy for computers, and start making them easy for humans and hard for computers.
The revolution has arrived. Are you ready to embrace it?
*For more insights on modern cybersecurity practices and Rhodium Systems’ approach to user-friendly security, visit our other Insight Articles or explore our comprehensive IT Operations Management solutions.